Helping Users Protect Themselves Against Scams

Client-Side Remote Access Tool Detection for Browser Sessions (AnyDesk & TeamViewer)
Executive Summary: Why Remote-Access Scams Are a Growing Risk
Remote-access scams are increasing globally because they do not rely on breaking authentication systems, they exploit human decision-making under pressure. In these attacks, victims are guided in real time by scammers impersonating banks, technical support, regulators, or internal security teams. Screen-sharing or remote-access software such as AnyDesk or TeamViewer gives the attacker visibility into the user’s device or direct remote control over the session.
From the perspective of traditional security systems, everything appears legitimate. Login credentials are correct, multi-factor authentication succeeds, the device’s reputation looks normal, and the transaction is technically authorized by the account owner. This makes remote-access scams particularly difficult to detect using conventional fraud prevention approaches.
For digital products that enable sensitive actions, such as payments, payouts, beneficiary changes, banking sessions, account recovery, or security setting updates, this creates a critical opportunity. By treating remote access being active during a sensitive session as a high-confidence risk context, organizations can intervene at precisely the moment when harm becomes irreversible.
This article explains why remote-access scams bypass traditional controls, how client-side browser detection can help, which detection signals are practical and privacy-aware, and how to design proportionate interventions that protect users without damaging trust or conversion.
The Business Problem: Customer-Authorized Fraud via Remote Control and Remote Utilities
Modern digital products are designed for speed, convenience, and self-service. These are essential characteristics of good user experience but they also create ideal conditions for social engineering attacks.
Remote-access scams are especially damaging for several reasons.
First, they turn legitimate customer journeys into fraud rails. The user is authenticated, on their own device, and performing actions that are normally allowed. Fraud systems that rely heavily on credential compromise or device anomalies often fail to flag these sessions.
Second, they suppress traditional warning signs. There is no account takeover in the classic sense, no bot-like behavior, and often no unusual geo location or device fingerprint. The attacker is simply guiding the victim step by step.
Third, they create significant downstream costs. Organizations face chargebacks, reimbursement obligations, customer complaints, regulatory scrutiny, and reputational damage. The customer narrative is often particularly painful: “I followed the instructions exactly and still lost money.”
Finally, regulatory expectations are evolving. In many markets, liability for authorized payment fraud is increasingly shifting toward service providers, especially when better preventative measures could reasonably have been applied.
The conclusion is clear: the trust boundary cannot stop at login. It must extend into the session itself and focus on high-impact decision points.
Why Traditional Fraud Controls Underperform Against Remote-Access Scams
Identity Verification Confirms the Person, Not the Influence
Authentication answers the question: “Is this the correct account holder?”
Remote-access scams require a different question: “Is the account holder acting independently and intentionally?”
When a user is being guided or coerced in real time, strong authentication alone is insufficient. The system confirms identity but cannot assess whether the user’s decisions are being externally controlled.
Security Education Is Usually Poorly Timed
Most scam education is delivered too early or too generically. Static warnings such as “We will never ask for your password” are easily overridden by a live scam script or malicious website. Victims are often told explicitly to ignore such messages.
Education is most effective immediately before a high-risk action, when the user still has the ability to stop and reconsider.
Manual Review Does Not Scale in Real-Time Journeys
Introducing manual review for every sensitive action would significantly degrade the user experience for legitimate customers. The objective is not universal friction, but selective friction applied only when strong contextual risk signals are present.
Post-Transaction Detection Is Too Late
Once a transaction has been completed, funds can be rapidly moved, split, or laundered. Investigations and reimbursements are costly and often unsuccessful. Preventing completion of the critical step is far more effective than reacting afterward.
Threat Model: What Remote-Access Scammers Are Trying to Achieve
Remote-access scams typically aim to manipulate users into performing one or more of the following actions:
- Adding a new beneficiary or payee
- Changing payout destinations (bank account, card, wallet)
- Initiating urgent or unusually large transfers
- Triggering account recovery flows
- Changing recovery phone numbers or email addresses
- Weakening security settings
What differentiates these scams from other forms of fraud is the attacker’s real-time presence. By seeing the screen or controlling the session, the attacker can guide the victim around warnings, accelerate completion, and maintain psychological pressure.
This is why remote access active during a sensitive session is such a powerful risk signal.
What Client-Side Browser Detection Can and Cannot Do
A browser environment is intentionally sandboxed. A webpage cannot enumerate installed applications or inspect other windows directly and it should not attempt to do so.
However, browsers can observe environmental side effects that often occur when certain remote-access tools are installed or running. This is best understood as collecting contextual telemetry, not monitoring user activity.
No single signal is definitive. The objective is to combine multiple weak signals into a calibrated risk score that justifies proportionate and reversible interventions.
Client-Side Detection Techniques to Detect Remote Access Attacks
Localhost Port Probing: Detecting Service Presence
Some remote-access or remote management tools expose local services to facilitate discovery or connectivity. A browser can attempt to connect to localhost on known ports and infer outcomes based on network-level behavior.
Even when cross-origin restrictions prevent reading responses, differences between connection refusal, timeout, or handshake behavior can provide useful signals.
This technique should be applied carefully:
- Only at high-risk moments
- With short, timeboxed probes
- Without logging raw responses
Used correctly, localhost probing can provide a strong “right now” signal that a remote-access tool may be active.
Font Fingerprinting: Identifying Installed Capabilities
Certain remote-access applications install distinctive fonts as part of their user interface. By comparing text rendering between baseline fonts and candidate fonts, a browser can infer whether these fonts are present on the system.
Font presence alone does not indicate an active session. However, it can signal that the device is capable of remote access, which becomes more meaningful when combined with in-session indicators.
This technique is passive, low-cost, and privacy-friendly when used to generate simple boolean signals.
Session Environment Cues: Viewport and Display Anomalies
Remote control and screen sharing can produce unusual combinations of:
- Rapid viewport size changes
- Uncommon aspect ratios
- Persistent full-screen or minimal-UI modes
These cues are highly ambiguous on their own. Many legitimate activities can produce similar patterns. As a result, environment cues should only be used as supporting evidence within a broader risk model.
Behavioral Signals: Identifying Guided or Coerced Users
When users are being coached in real time, their interaction patterns often change common indicators include:
- Segmented typing with pauses, suggesting reading or dictation
- Long hesitation on confirmation steps
- Indirect or searching mouse movements
- Extremely fast or unusually slow task completion
Behavioral analytics do not need to be complex to be effective. Simple heuristics can provide meaningful signals, especially when aligned with high-risk journey steps.
Evaluating Detection Signals and Minimizing False Positives: Strengths, Weaknesses, and Safe Defaults

Each category contributes to partial confidence. Together, they support defensible intervention decisions.
To remain privacy-safe and trustworthy, organizations should apply strict constraints:
- Collect minimal, coarse-grained signals
- Limit checks to high-risk moments
- Retain data only for calibration
- Be transparent about the purpose of detection
- Report suspicious activity to administrators
- Ensure processes scale across the enterprise
Designing Scam-Resistant Interventions That Break Real-Time Control
Scammers actively coach victims to bypass warnings. Effective interventions must therefore be difficult to complete while under coercion.
High-impact patterns include:
- Forced re-authentication using device-bound methods
- Active intent confirmation requiring meaningful user input
- Cooling-off periods for new or high-value changes
- Verified safe-exit paths to trusted support channels
Language is critical. Copy should normalize the situation, avoid blame, and clearly explain why an action is being paused.
Operational Readiness: Aligning Support and Fraud Teams
Introducing session-based interventions will change user behavior and support contact patterns. Preparation is essential.
Support teams need clear scripts, decision trees, and disposition categories. Fraud and risk teams need policy thresholds, exception handling rules, and regular calibration loops.
Consistency is vital. Ad-hoc overrides create confusion and new vulnerabilities.
Practical Phases of Client-Side Detection
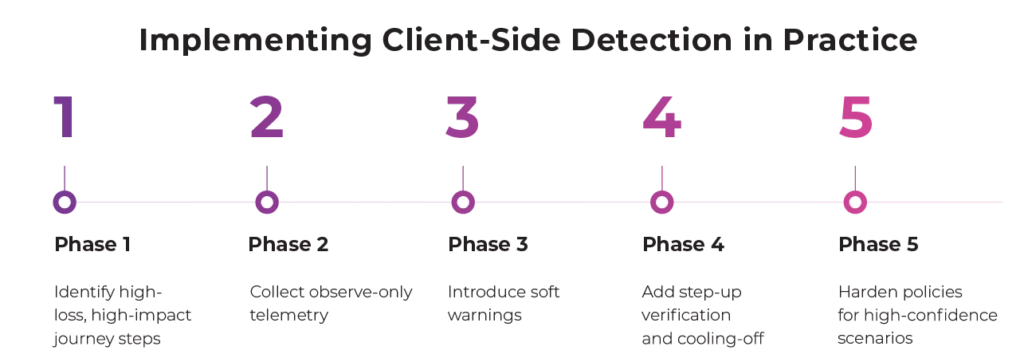
Client-side detection should act as a signal provider. Final decisions should be made by backend risk engines that combine session context with transaction history and server logs.
Strategic Context: Why Session-Level Security Is Becoming Essential
Remote-access scams are part of a broader trend toward industrialized social engineering. Attackers continuously refine scripts and tooling, while regulators increasingly view authorized fraud as preventable.
In this environment:
- Authentication is necessary but insufficient
- Session context is a core security control
- The web browser is a critical intervention point
- Administrators and IT professionals worldwide must manage risk carefully
Organizations that adapt will reduce losses and strengthen customer trust.
Precision Safeguards Create Durable Trust
Remote-access tools like AnyDesk and TeamViewer are not inherently malicious. However, when active during sensitive moments, they represent a high-risk context that demands attention.
The most effective strategy is not blanket blocking or invasive monitoring. It is precision safeguards: minimal, privacy-aware detection combined with proportionate, well-designed interventions.
By focusing on irreversible moments and breaking real-time attacker control, organizations can protect users, reduce operational costs, and build lasting trust in digital experiences.
